About Us
We are GRM, a CERTIN Empaneled Cyber & Information Security Audit, Advisory, Consulting Company that helps enterprises to store, process, and access data in a secure manner.
We help our clients reduce organizational risk and strengthen all defenses, and build customer trust.
Founded in 2013, our company was launched with a view to protect and preserve the integrity of client organizations’ systems and data. Our team of 15+ industry-certified security professionals, headquartered in Chennai, India, possess deep and extensive knowledge of threat vectors, security standards, government regulations, and data protection laws.
We offer a wide range of comprehensive and professional Cybersecurity & Information Technology Security solutions to suit a variety of organizational needs and types.
In close collaboration with client teams, we also carry out business risk assessments through risk mitigation planning and security benchmarking, ensuring compliance with your cybersecurity frameworks such as ISO27001, NIST, SOC2, HIPAA, GDPR among others.
In short, we are your one-stop Cybersecurity partner
for everything.
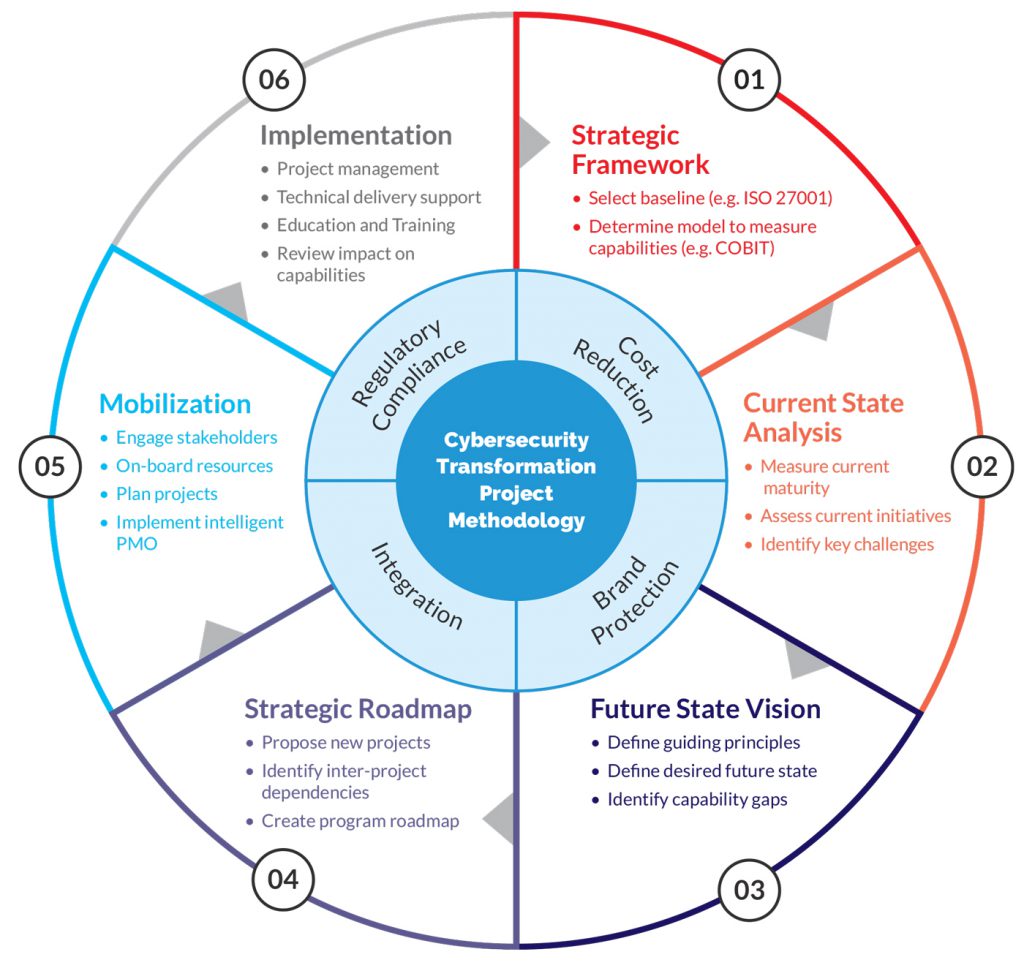
Cybersecurity Transformation Project Methodology
- Cost Reduction
- Integration
- Brand Protection
- Regulatory Compliance
Our Approach to Securing Enterprise
For enterprises to operate fearlessly, the need of the hour is to understand the hacking methodology to mitigate risks, and stay ahead by establishing a digital security framework early on. GRM has a 4-pronged, technology focused, strategic approach to build and implement any security requirement that ensures 100% coverage of all types of risks and threats.
TECHNOLOGY-LED ENGAGEMENT MODEL
ASSESS
Identify security risks and business requirements
ADVICE
Provide most fitting solutions based on global frameworks
ASSIST
Extend support for the entire Implementation Lifecycle
ADOPT
Cybersecurity and information security engagements across verticals
We use proprietary toolsets and advanced technologies to implement Cybersecurity and Information Security plans, and we proactively test and develop effective ways to secure key elements of our client’s network and devices.
Using a set of tested and established best practices, leading applications, and a robust framework, we assess the cybersecurity risk to the business environment and present a detailed report with precise guidance on the actions that enterprises can take to secure the business.
Our domain expertise enables business operations to mitigate security threats, address all security issues that may cause intense damage to data and information, and comply with Legal and regulatory requirements.
With our services and solutions, enterprises can implement cost competitive security measures for the long term, and enhance ROI.
Cybersecurity Transformation Framework
What Client’s Say About Us
GRM Technologies has been serving as our trusted partner and cybersecurity advisor. The team at GRM has an intuitive sense of our business climate and work closely with us to respond to our security challenges. The governance framework laid down by the team at GRM has enabled us to better prepare, protect, detect, respond, and recover from a wide range of cyber threats.
Ganesh Duraiswamy
Head – Operations IVY MobilityThe integrity and passion of the team at GRM has served as a foundation of our relationship with them. Their technical acumen and strategic roadmaps have enabled us to go from strength to strength in terms of our cybersecurity posture. We attribute significant savings to GRM Technologies on account of their cybersecurity, risk advisory, and effective training services for our employees.
